Android Security - Part 1
Android is such a beautiful world, full of unicorns and…
Wait a minute, is that so?
What is hidden under the hood? This is the core of lesson 2: Android Security, Part 1.
Simone Aonzo (packmad), our Android guru, charmed the audience with his lesson, uncovering what’s inside the Android operating system.
Everyone knows that Android applications are written in Java.
This is compiled into Dalvik bytecode, which is executed by a virtual machine.
Bytecode can be decompiled: each .apk can be opened and modified as you please.
Trust me, I’m not joking at all.
This is the crucial point of this class: it is easily possible to open an application, modify it and re-compile it again.
This pipeline produces a brand-new application, which could probably behave differently in respect to the original one. Aren’t you satisfied yet?
It’s time to dirty your hands! Here you can download a simple .apk file, crafted by packmad himself.
Using apk-tools you can decompile it and edit the code… and do very very mean things.
There are hidden flags in that application, can you collect all of them? :-)
Next lesson will cover aspects of Reverse Engineering, stay tuned!
146 154 141 147 173 142 145 137 163 155 141 162 164 137 142 145 137 141 156 144 162 157 151 144 175 :-D

- Can you remember each of those Android Version?

- Java seen from the cameraman.
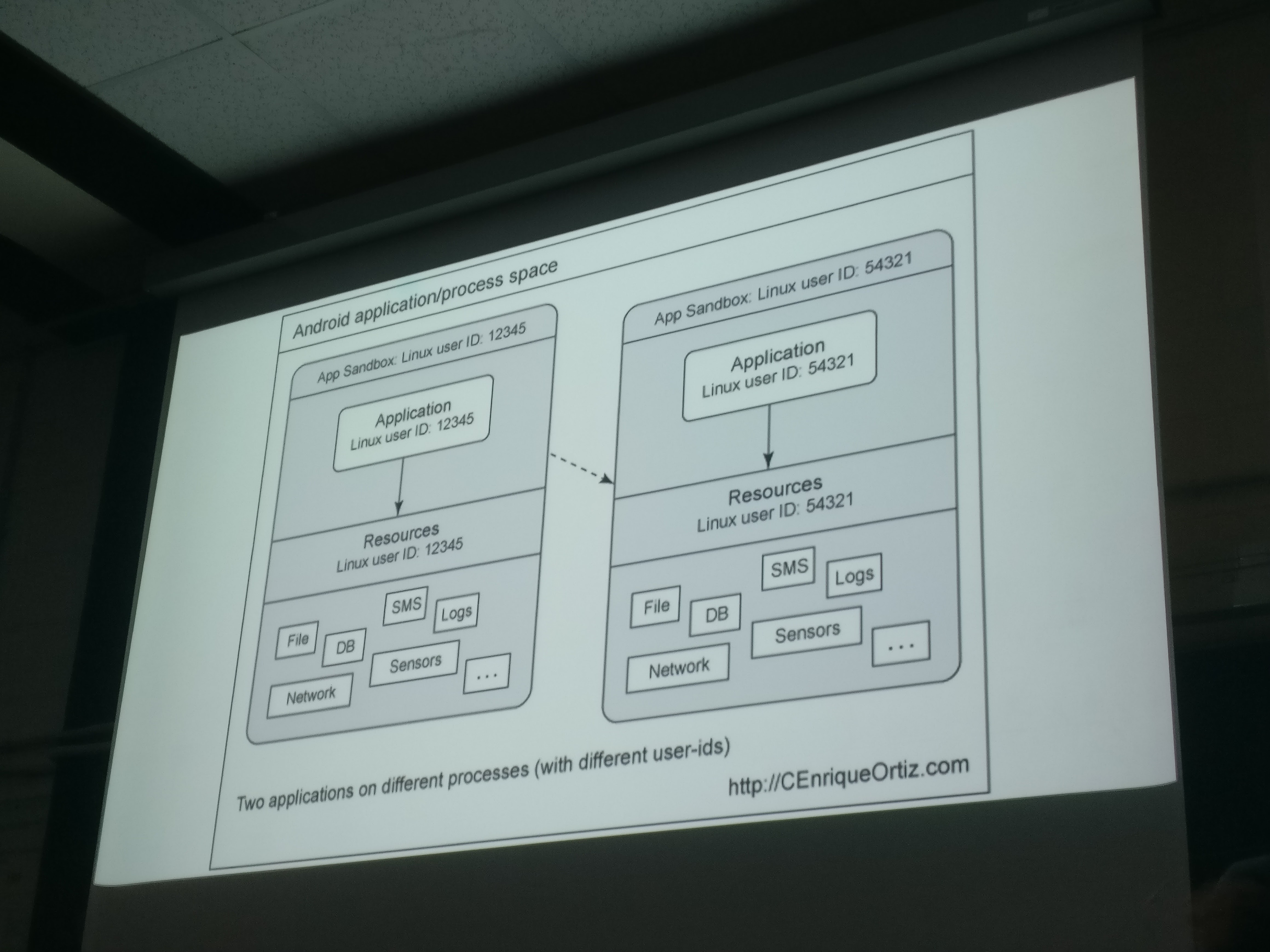
- How Android manages processes.
- Connections explained fast.

- Lesson is over, it’s time for a break!

- packmad hacking the application.

- See you next time!