Binary Reversing - Part 2
The fourth lesson is the natural consequence of its predecessor: Binary Reversing, Part 2.
zxgio begins with the whole suite of IOLI Crackme binaries, using Radare2 to pwn them.
What does mov instruction do? And cmp?
Or what is that strange lea eax, [ebp - 120]?
The ultimate secret to reversing a binary lies in only one word: Assembly.
Assembly (often abbreviated to asm) is the nearest programming language to machine instructions. In the end, every program is translated into Assembly: if you know how to deal with it, you’re done with reversing.
Why is Radare2 so useful? It offers a disassembler, a step-by-step debugger, interaction with system registers and so on. In order to crack the password from those binaries, you need to interact with Radare2, which is not easy at all.
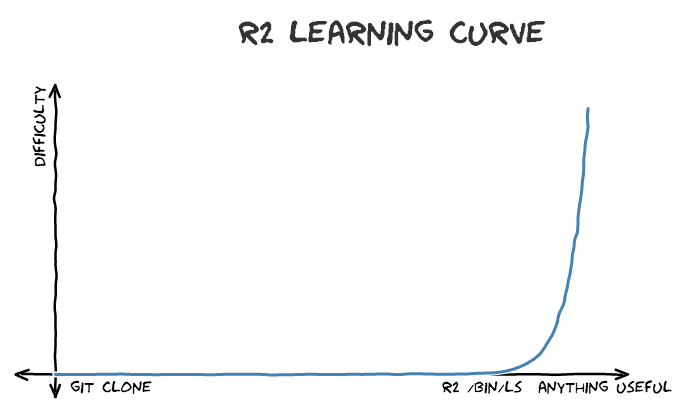
Want more? Here you can find zxgio Radare2 cheatsheet (for free, of course), which is a useful summary of Radare2 commands. No need to feel lost, just read that sheet!
IOLI Crackme-s were fun to hack, but what about something more difficult? Just look up at learning section of this website to consider more challenging tasks…
Binary reversing classes are over! Web Security - Part2 is the next lesson to come!
Have fun with Radare2 ;-)
@iH<,{5vLRWsjmzhZ}L=a^w:H T.T

- A brief introduction before the class.

- zxgio showing how to pwn a binary.

- Students are working hard. Keep calm and reverse that binary.

- Even Prof. Ribaudo has been spotted reversing binaries!
- Radare2 here, Radare2 there.

- Assembly is strong in this man.

- See you next class!