Web Security - Part 2
You understood that SQL Injections are evil. So, you open your browser and type “how to sanitize input in php”.
You find that exists a beautiful mysql_real_escape, which claims to remove all escape sequences.
This means that all the injections seen during the previous class can’t be unleashed in this new scenario.
… or so it seems.
It is time for avalz to show us new techniques: this is Web Security Part 2!
So, how that function works? Basically, it appends a ‘' to each escape character, which turns to a standard character. It’s not the time to be lazy because not all the attacks can be stopped with this trick.
Why?
Imagine you have a number as payload instead of a string such as:
SELECT * FROM users WHERE id=$id
the $id parameter is an integer.
It is totally legit to do that! Instead of that tiny number, I can put everything on it!
I can even use errors as a vector of an information leak. For example, if you echo the error generated by your last query…
Follow the live stream to collect all the details and master this new powerful leaks.
This concludes Web Security!
MZWGCZ33JFPWQYLUMVPVASCQPU====== -.-“

- avalz starts his class with a brief recap.
- W3challs, we don’t fear you.

- Attacks done well.
- That message is not so friendly, isn’t it?
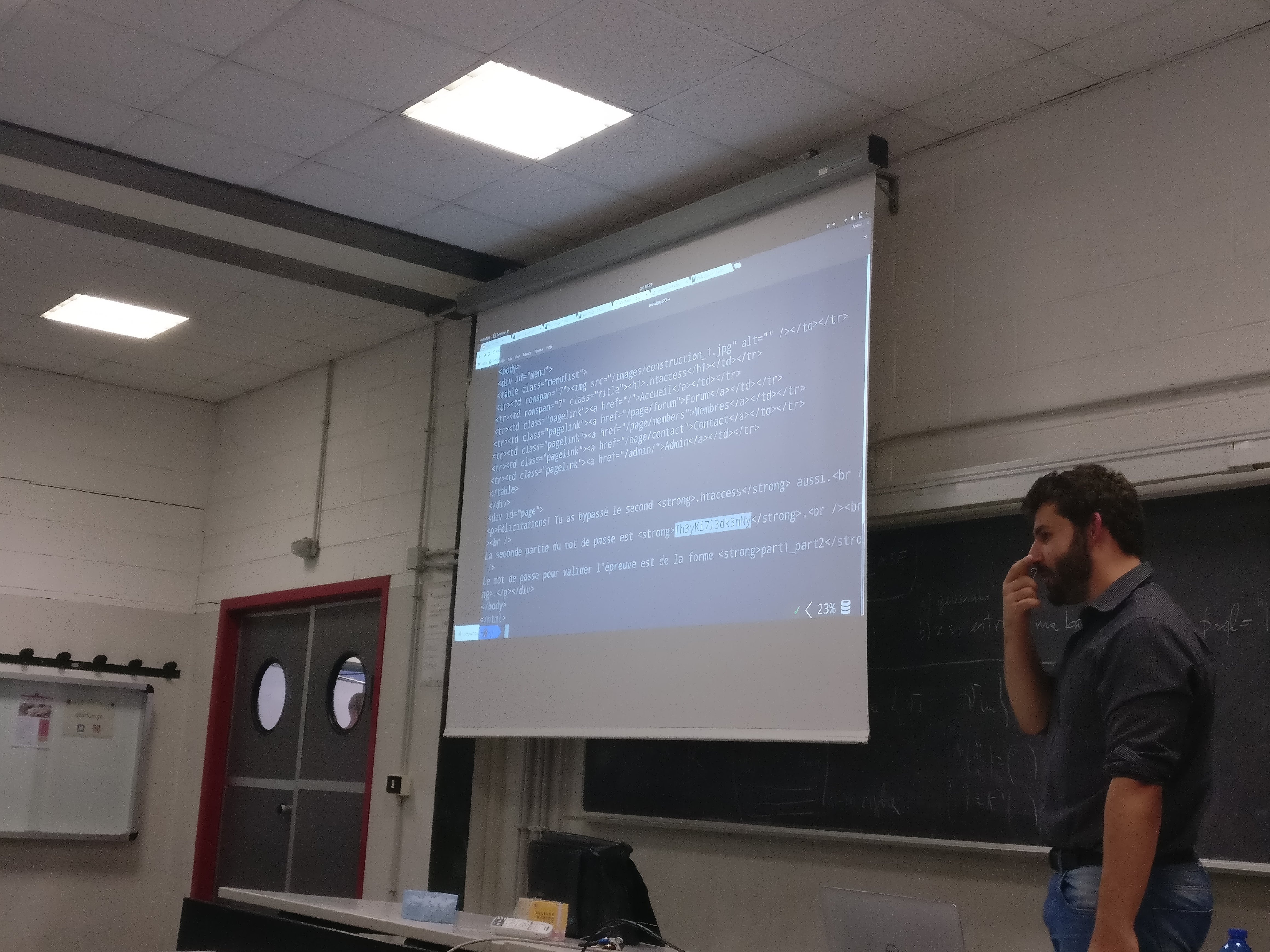
- Explore the source to understand how that challenge works!

- Thank you again!