Reply Cyber Security Challenge - Tangle
revR-Boy is sure the Rebels are planning something! Immediately, he starts looking for their plan. Indeed, the Rebels have been careless! On a different port on the same host, R-Boy uncovers a strange binary application, which surely hides a key. Oh no, R-Boy definitely needs help!
First of all, I tried to run the program…but…
sh
$ ./tangle
$
Nothing happened…let’s find out why..
So I tried to run it using ltrace to see if it does something background.
sh
$ ltrace ./tangle
+++ exited (status 255) +++
But even this time, nothing.
For this challenge I decided to use Cutter, with that was easily to see that the main receive 2 args, so i tried to do ltrace with 2 arguments.
sh
$ ltrace ./tangle first second
strlen("first") = 5
+++ exited (status 255) +++
I descovered it calls strlen on the first argument and then exits.
By analyzing the code I could see that the program calls many times strlen on the first argument and check if there are 2 arguments, all this steps are useless and redundant.
Sometimes there are also some piece of code that check needlessly if a character of the first argument is equal to itself.
What are needed to find out the flag are the parts like this one:
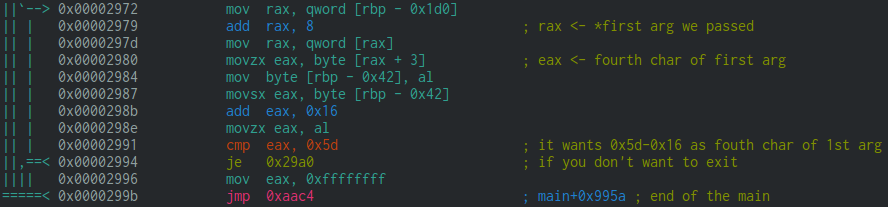
Where it takes a char in the first argument to check if it is part of the flag…
In conclusion the flag was: {FLG:R3memb3RY0uRch1ld0od!}