Flare-On Challenge 7 - 01 - Fidler
revWelcome to the Seventh Flare-On Challenge!
This is a simple game. Win it by any means necessary and the victory screen will reveal the flag. Enter the flag here on this site to score and move on to the next level.
This challenge is written in Python and is distributed as a runnable EXE and matching source code for your convenience. You can run the source code directly on any Python platform with PyGame if you would prefer.
The challenge consists of a simple game written in python, you are given both the precompiled executable and python source code.
First of all the challenge ask you for a password, by opening fidler.py it’s easy to see the check_password function that asks you to input ghost.
Once the password is checked the game starts.
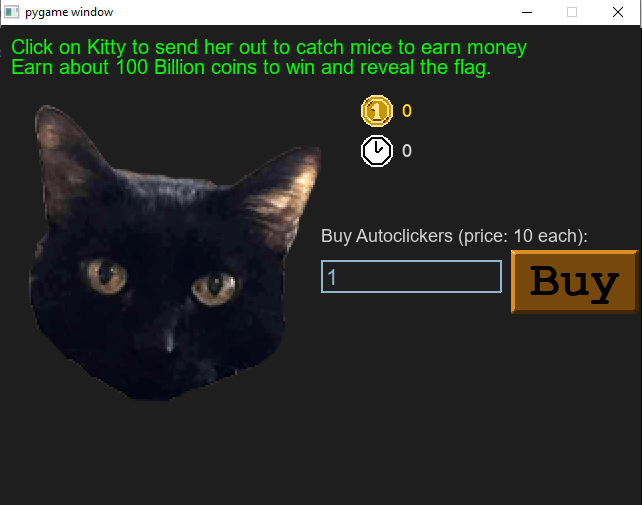
To obtain the flag you have to reach 100 Bln clicks, you can buy auto-clickers paying already done clicks. Even with auto-clickers, reaching 100 Bln clicks, it’s obviously a stupid idea and not the intended solution.
Looking in the source code, in fidler.py, there is a function:
def decode_flag(frob):
last_value = frob
encoded_flag = [1135, 1038, 1126, 1028, 1117, 1071, 1094, 1077, 1121, 1087, 1110, 1092, 1072, 1095, 1090, 1027,1127, 1040, 1137, 1030, 1127, 1099, 1062, 1101, 1123, 1027, 1136, 1054]
decoded_flag = []
for i in range(len(encoded_flag)):
c = encoded_flag[i]
val = (c - ((i%2)*1 + (i%3)*2)) ^ last_value
decoded_flag.append(val)
last_value = c
return ''.join([chr(x) for x in decoded_flag])
def victory_screen(token):
...
flag_content_label.change_text(decode_flag(token))
...
The function victory_screen is called as follows:
victory_screen(int(current_coins / 10**8))
Where current_coins is the number of clicks done.
So retrieving the flag could be done by calling the decode_flag function.
idle_with_kitty@flare-on.com