Flare-On Challenge 7 - 05 - TKApp
revNow you can play Flare-On on your watch! As long as you still have an arm left to put a watch on, or emulate the watch’s operating system with sophisticated developer tools.
This challenge gives you a TPK file. A TPK file is a Tizen Application Package file and it is used on watches running Tizen OS.
As for Android applications, we can unzip it to take a look at the components. Inside the bin folder can be found a bunch of dlls, they were written and compiled in C# so dnSpy can be used to analyze them.
During the analysis of TKApp.dll I noticed a sort of “anomaly”. The MainPage class has a GetImage method that is going to read and decipher a resource called “Runtime.Runtime_dll”.
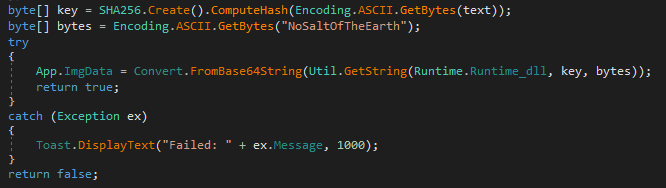
So I decided to decipher the content of that resource as it does the application. The key used to decipher the flag is generated by hashing the text variable, generated as follows:
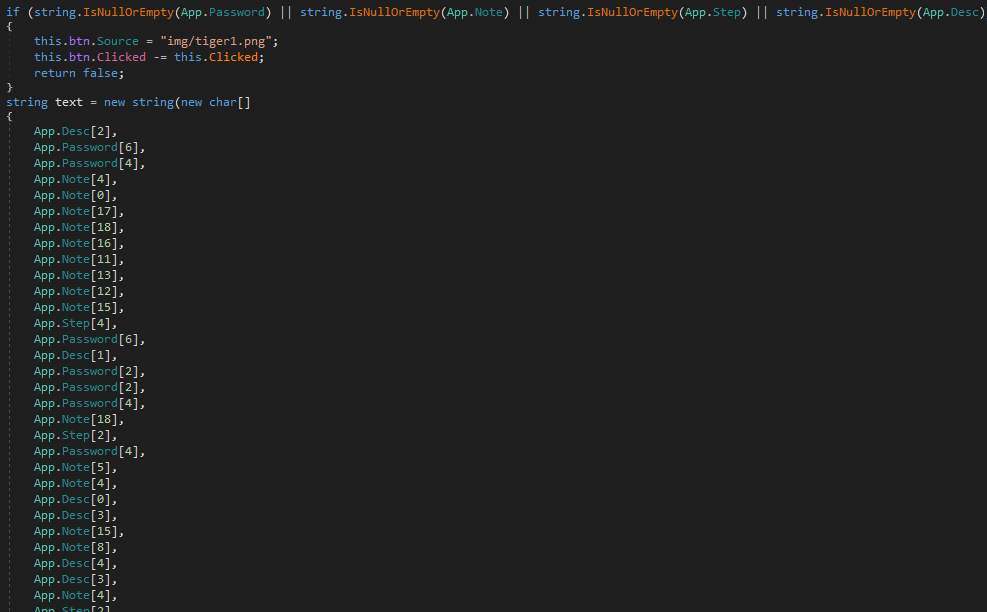
All the variables used are initialized in other points of the application upon specific circumstances, so to check that I was using the right values I found another point in the code where I could test these variables.
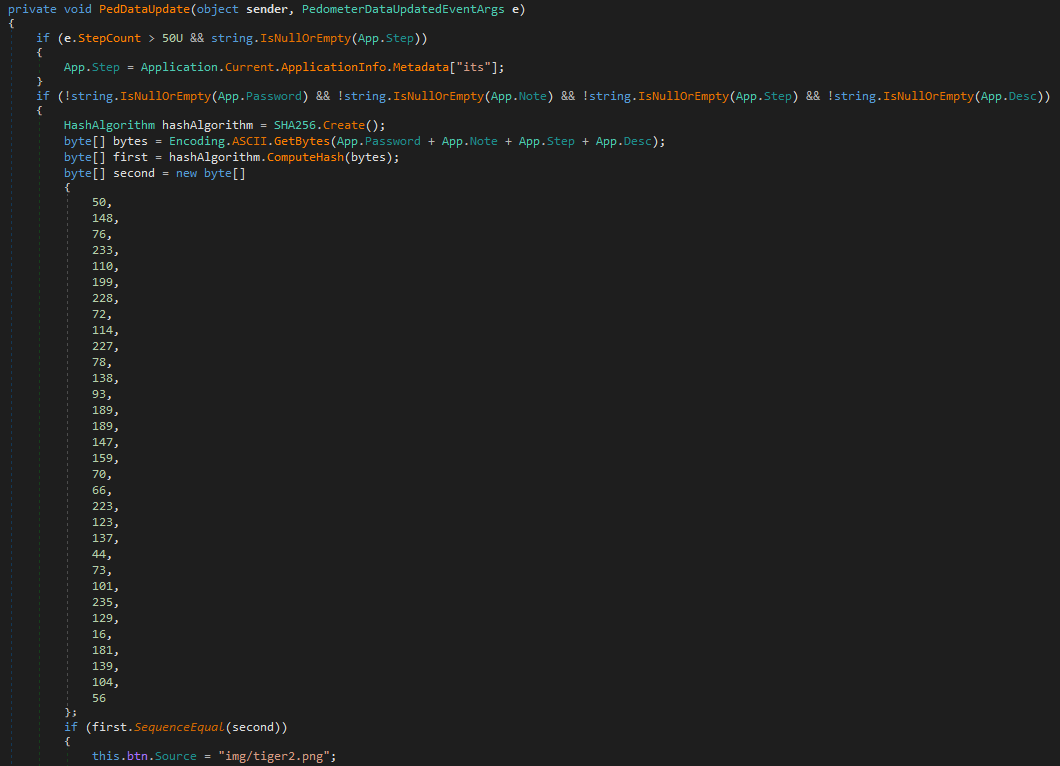
As shown in the image they are used to generate a hash that must be equal to the one hardcoded.
Once found the right variables the Runtime_dll resource can be decrypted.

n3ver_go1ng_to_recov3r@flare-on.com